- FR
- EN
Triton Cyber Attack: hackers target the safety systems of industrial plants
The incident, publicly disclosed in December 2017, occurred when hackers successfully infiltrated the critical safety systems of an unidentified industrial facility, reported to be located in Saudi Arabia.

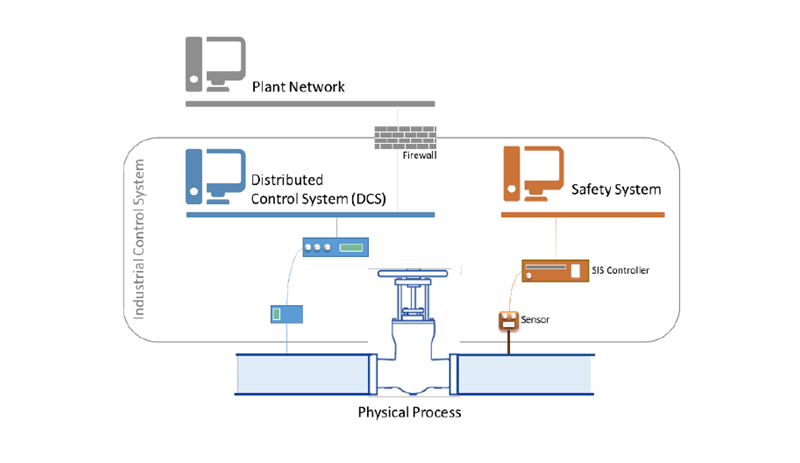
The attack launched a malware designed to manipulate Industrial Control Systems (ICS), which allow the control and monitoring of industrial facility processes, as depicted below in Figure 1.
The malware, dubbed “TRITON”, is an attack framework designed to interact with Triconex Safety Instrumented System (SIS) Controllers, specifically a component named “Tricon”, manufactured by Schneider Electric SE and commonly used in several industry sectors[1]. The Tricon controllers are essential in monitoring certain aspects of the operating environment (e.g. temperature/pressure) of an industrial facility and enable the shutdown of processes in the case of the detection of potentially dangerous readings (i.e. the “failsafe” mode).
In this event, the attack was identified by staff when some processes at the targeted facility were inadvertently shutdown, as the hackers deployed the TRITON attack framework in an attempt to reprogram the facility’s SIS controllers. The failure of the attack was thought to be the cause of a bug in the script of the malware, accidentally causing the emergency system to activate the shutdown procedure.
According to an assessment of the event by the cybersecurity company FireEye, it is thought that the motive of the attack was to develop the capability to infiltrate and reprogram the automated safety systems of key industrial facilities, with the probable intention of causing physical damage and disruption to critical infrastructure.
POTENTIAL VULNERABILITIES OF THE TRICON CONTROLLERS AND PREVENTION
The TRITON malware is reported to have exploited a “Zero-day flaw” in the Tricon controllers. This flaw enables the malware to scan and map the ICS of the facility to provide reconnaissance and issue commands to the Tricon controllers via a remote network connection. However, the malware can only be successfully deployed if the controller is switched to the “PROGRAM” mode.
In a recent security update from 18th January, Schneider Electric stated that the vulnerability detected is limited to a small number of older versions on the Tricon component and emphasised that the evidence gathered indicated that if the system key switch had been left in the recommended position, the malware injection would have failed.
Schneider is currently finalising a security patch which will detect the malware’s presence in a Tricon controller, before deploying a procedure to remove it.
ATTACK CONTEXT AND PERPETRATORS
TRITON is one of a small number of identified malicious software families that target industrial control systems. These have included “Stuxnet”, that was used against Iran in 2010 and “Industroyer”, which is believed to have been used in an attack that cut power in Ukraine in 2016. However, TRITON is slightly different, in that this is the first known case of an attempt made to attack safety instrumented system (SIS) devices. The significance of this is that if successful, an attack could go unnoticed until a critical failure occurs.
Although the perpetrators of this attack have not been identified, FireEye concluded that the actor is likely to be sponsored by a nation state, intent on preparing for a high-impact attack with physical consequences. The facts contributing to this reasoning were; i) the targeting of critical infrastructure, ii) the attacker’s persistence (considerable amounts of planning and technical resources were required) and iii) the absence of a clear monetary goal.
IMPLICATIONS OF THE ATTACK FOR THE TARGETED COMPANIES
This attack targeted critical infrastructure with the potential to cause losses on many levels. These could include direct physical damage and loss of life in the case of an explosion at the targeted facility, in addition to wider impacts, including business interruption losses.
RECOMMENDATIONS
It should be emphasised that the type of cyber attack documented here, requires specialist knowledge and considerable planning to be successfully executed and is therefore more likely to be committed by a well-funded nation state with a political motive. In this context, it is important that risk management strategies consider the current geopolitical risk environment of the countries in which they operate.
In terms of specific safety recommendations, Schneider Electric is due to release a security patch that will neutralize this vulnerability in older versions of the Tricon SIS controller. Apart from deploying this patch as soon as is practicable, more general security recommendations can be found in an updated security notification issued by Schneider Electric on 18th January 2018. The key elements of these recommendations are:
- Ensure that the safety systems are isolated from all other external networks.
- The safety controllers should be secured and accessible only by authorized personnel. In addition, the controllers should never be left in “PROGRAM” mode by default.
More generally, although this particular case seems to have been an isolated incident, it raises broader concerns regarding the concentration risk inherent in the safety systems of industrial plants. Of particular concern is the targeting of weaknesses in components that are known to play a central role in maintaining the safe operation of a variety of critical infrastructure facilities.
Authors
Rebecca Cheetham - Group Senior Risk Manager
Sébastien Heon - Cyber Expert at SCOR
Sources
- FireEye Blog: https://www.fireeye.com/blog/threat-research/2017/12/attackers-deploy-new-ics-attack-framework-triton.html. December 14, 2017.
- The Guardian: https://www.theguardian.com/technology/2017/dec/15/triton-hackers-malware-attack-safety-systems-energy-plant. 15 December, 2017.
- Security Notification from Schneider Electric - Malware Discovered Affecting Triconex Safety Controllers v2: https://www.schneider-electric.com/en/download/document/SEVD-2017-347-01/. January 18, 2018.
- ZD Net: http://www.zdnet.com/article/triton-exploited-zero-day-flaw-to-target-industrial-systems/. January 19, 2018.
[1] Refining & Petrochemicals, upstream & midstream oil and gas, chemicals, power generation, pharmaceuticals - https://www.schneider-electric.com/en/work/products/industrial-automation-control/triconex-safety-systems/logic-solver/tricon.jsp